Access control is the control of entrances and exits, managing who can enter and exit at what time, and can automatically generate various reports to provide post-event record information. When the access control equipment is installed in the access passage, when people need to pass through, it is necessary to carry out the appropriate level of authority identification to distinguish whether they can pass through. Generally, the authority of the passer can be represented by a card, fingerprint, iris (eye), and the identity of the passer can be identified.
Access control system, also known as access control system (ACCESS CONTROL SYSTEM), is an intelligent management system for managers to enter and exit. It integrates modern security management measures and microcomputer automatic identification technology, and is the product of many advanced technologies such as machinery, communication technology, computer technology, electronics, optics, and biotechnology in the field of access control management. It is an effective measure for important entrances and exits to realize safety prevention management. The access control system has developed rapidly in recent years and is widely used in management control systems.
The access control system plays an irreplaceable role in the construction of data centers. With the continuous advancement of science and technology and the continuous improvement of informatization, the functions of the access control system are also continuously improved. Although the access control system is not very important in the construction of the computer room system, it is an indispensable part.
The access control system is generally composed of a controller, a card reader, an induction card, an electric lock, an integrated management server, a system management workstation, a card system, etc. It can implement hierarchical management and computer network control.
At present, the relatively complete setting of the access control system of the data center is that you may only need to swipe the card to enter the building, you need to swipe the card and password to enter the computer room, the password and biological scanning may be required in the core area, and two-way swipe card.
So what are the functions of the access control system?
1. Access control and channel access control: prevent the entry and exit of non-card personnel and illegal card holders.
2. Statistical function: Statistics are made according to employee departments, categories, and different access times and locations.
3. The function of preventing illegal entry: The access control system can manage at least 100,000 black and white lists. If an unauthorized card or a card in the system blacklist is used, the system will refuse to open the door lock and automatically call the police through a reservation procedure and device.
4. Prevent illegal time entry function: timetable can be set, if certain time periods can be regarded as illegal time, cardholders can not enter; you can always check the entry and exit sites, personnel entry and exit conditions in each time period.
5. Anti-removal function: Each front sensor is integrated with the wall of the installation place when it is installed, and cannot be removed at will.
6. Anti-theft function: When the criminals sneak into the crime, the access control system automatically closes all the access control after receiving the alarm.
7. Anti-theft function: The access control system is equipped with a rear power supply to prevent power failure.
8. Anti-involvement function: The access control system has the function of preventing one access control from being damaged and affecting the normal work of other access controls.
9: Card stealing function: In the case of using a password keyboard, the cardholder must enter the password after swiping the card to perform dual identity authentication to prevent the adverse consequences caused by the loss of the card.
10. Anti-return function: key access control, all cards must be swiped to enter the card before swiping out, and vice versa.
11. Inquiry function: It can inquire the records of entry and exit of anyone at any time at any time.
12. Double-door linkage function: The access control system can set the authority to force that the other doors cannot be opened when a door is opened, and only certain doors can be opened or closed when a door is opened afterwards.
The reasonable use of the access control system greatly improves the security and reliability of the data center computer room and avoids the losses caused by the chaotic entry of personnel. It can be said that the access control system is an important barrier for the security of the data center.
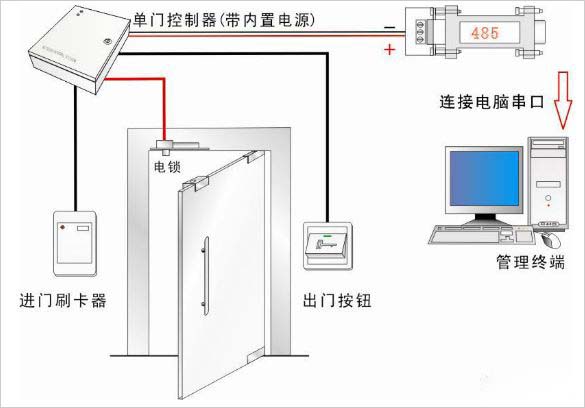
The type of access control system and its respective advantages and disadvantages, scope of application:
1. Non-networked access control: a host correspondingly controls and manages a door, which is directly controlled by the controller, and cannot be controlled by computer software. Advantages: cheap price, simple installation and maintenance. Disadvantages: No entry and exit records. Scope of application: It is not suitable for places where the number of doors is more than 5 sets, the number of people is greater than 50, or the flow of personnel is large, and personnel are frequently recruited and resigned.
2. 485 networked access control: directly use computer software for management control, including card and event control. This access control can communicate with the computer. Advantages: centralized control, convenient management, you can view records, and analyze and process records for other purposes. The training is simple and can provide value-added services such as attendance. Disadvantages: higher prices and more difficult installation and maintenance. Scope of application: suitable for places with large number of doors, large number of people and frequent movement of people.
3. TCP / IP access control: It is also called Ethernet network access control. It connects the computer and the controller through a network cable. It is an access control system that can be networked. Advantages: In addition to all the advantages of 485 networked access control, it also has the advantages of faster speed, easier installation, larger number of networks, and cross-regional or cross-city networking. Disadvantages: high price, requires professional network knowledge. Scope of application: suitable for installation in large projects, large number of people, speed requirements, and cross-regional projects.
4. Fingerprint access control system: Access control managed by fingerprint instead of card. Advantages: It has the same characteristics as 485 networked access control, but it has higher security. Disadvantages: The number of people that can be managed is small, and the passing speed is slow.
Keychain,High Quality Keychain,Keychain Details, CN
Dongguan Maimeng Cultural Communication Co., LTD , https://www.icollectoys.com